A critical security flaw has been uncovered in a widely-used authentication protocol, potentially putting countless enterprise and telecommunications networks at risk. Researchers from the University of California San Diego have identified vulnerabilities in the Remote Authentication Dial-In User Service (RADIUS) protocol that could allow attackers to gain unauthorized access to network devices and manipulate network traffic.
The RADIUS Protocol: A Legacy System with Modern Implications
RADIUS, developed in 1991 during the era of dial-up internet, remains a crucial component in modern network infrastructure. It allows networked devices such as routers, switches, and mobile roaming equipment to validate login credentials through a remote server. This centralized approach to credential management has made RADIUS a cornerstone of enterprise and telecommunications networks, often controlling access to tens of thousands of switches in large organizations.
Despite its widespread use, the protocol has received surprisingly little scrutiny from the academic cryptography and security communities. Nadia Heninger, a professor in the Jacobs School of Engineering Department of Computer Science and Engineering at UC San Diego, highlights this oversight: “Given how widely this protocol is used, it is surprising that it has received almost no formal security analysis in the academic cryptography and security communities.”
Blast-RADIUS: Exploiting Decades-Old Weaknesses
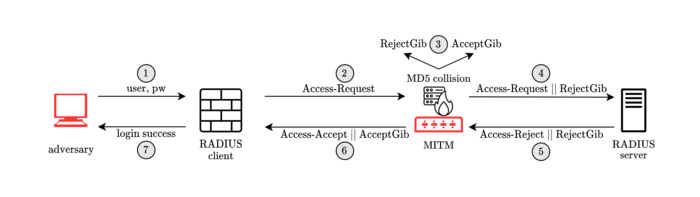
The newly discovered vulnerability, dubbed Blast-RADIUS, stems from the protocol’s outdated cryptographic design. RADIUS relies on an authentication check based on the MD5 hash function, which has been known to be insecure for nearly two decades. This weakness allows for a “man-in-the-middle” attack, where an attacker can intercept communication between a RADIUS client (the victim’s networked device) and the RADIUS server, forging a valid protocol accept message in response to a fake login or authentication request.
The implications of this vulnerability are severe. An attacker could potentially gain administrative access to networked devices and services without needing to guess or “brute force” passwords. This level of access could allow malicious actors to manipulate network traffic, access sensitive data, or even use compromised devices as a launching point for further attacks.
The research team’s findings, presented at the USENIX Security 2024 conference, have led to one of the largest and most complex vulnerability disclosure processes in recent memory. More than 90 vendors have been involved in a coordinated disclosure and have issued security bulletins in response to the discovered flaws (CVE-2024-3596 and VU#456537).
Why it matters: The Blast-RADIUS vulnerability affects a fundamental protocol used in countless enterprise and telecommunications networks worldwide. Its discovery highlights the ongoing security risks posed by legacy systems that have not been updated to meet modern cryptographic standards. For businesses and organizations, this serves as a crucial reminder of the importance of regularly auditing and updating even the most established network protocols.
For network administrators and IT professionals, immediate action is required. Vendors have released patches implementing the researchers’ recommended short-term mitigations for this vulnerability. System administrators should promptly check for patches for protocols they use with RADIUS and apply the updated configuration options suggested by their vendors.
The discovery of the Blast-RADIUS vulnerability also underscores a larger issue in the cybersecurity landscape: the gap between those who deploy protocols and those who study them. As our digital infrastructure continues to evolve, bridging this divide becomes increasingly crucial to ensure the security and integrity of our networks.
As organizations worldwide rush to patch their systems, this incident serves as a stark reminder of the persistent vulnerabilities that can lurk in even the most widely-used and long-standing protocols. It emphasizes the need for ongoing security research and the importance of regularly updating and securing all aspects of our digital infrastructure, no matter how established they may seem.